New Format for The Bar Chart Reference Page
The Data Visualisation Catalogue
DECEMBER 13, 2021
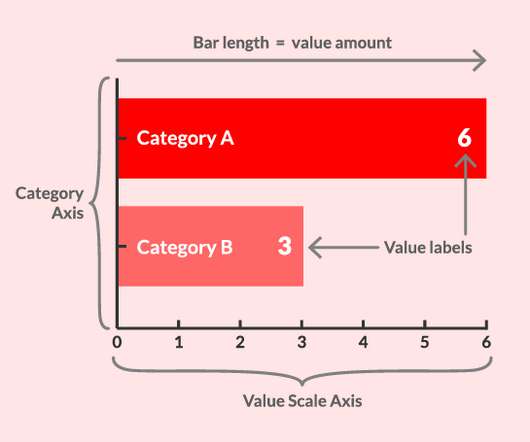
User Modeling and User-Adapted Interaction , 16(1), 1–30. Eurographics Conference on Visualization (EuroVis) , 34. Bar charts and box plots. Streit, M., & Gehlenborg, N. Nature Methods, 11 (2), 117. Four Experiments on the Perception of Bar Charts. Setlur, V., & Anand, A. Carberry, S., & Hoffman, J. Zacks, J., & Tversky, B.











































Let's personalize your content