Risk Management for AI Chatbots
O'Reilly on Data
JUNE 27, 2023
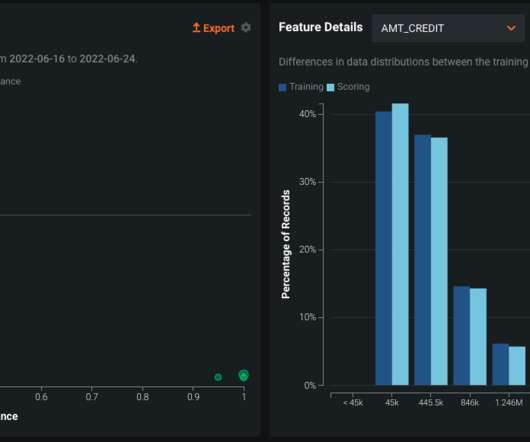
Welcome to your company’s new AI risk management nightmare. Before you give up on your dreams of releasing an AI chatbot, remember: no risk, no reward. The core idea of risk management is that you don’t win by saying “no” to everything. So, what do you do? I’ll share some ideas for mitigation.














































Let's personalize your content