Optimization Strategies for Iceberg Tables
Cloudera
FEBRUARY 14, 2024
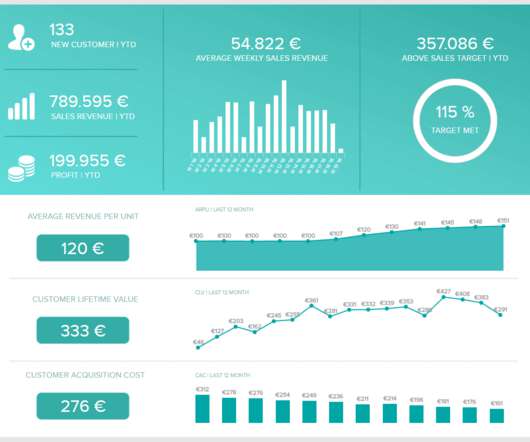
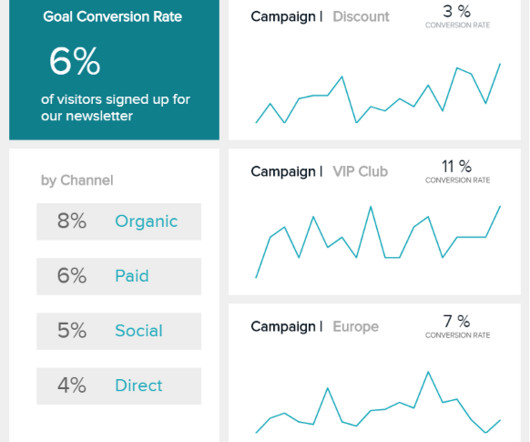
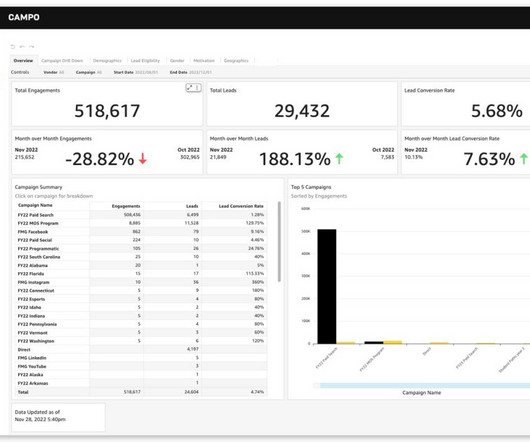
This blog discusses a few problems that you might encounter with Iceberg tables and offers strategies on how to optimize them in each of those scenarios. You can take advantage of a combination of the strategies provided and adapt them to your particular use cases. You could also change the isolation level to snapshot isolation.











































Let's personalize your content