Data Strategy Creation – A Roadmap
Peter James Thomas
MARCH 17, 2020
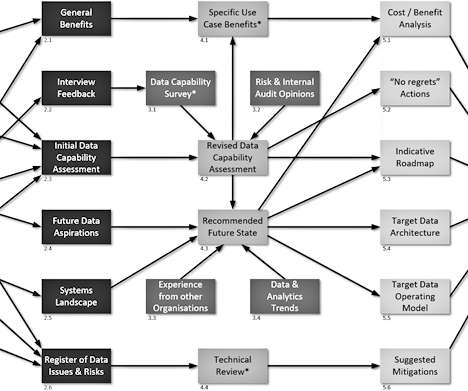
Data Strategy creation is one of the main pieces of work that I have been engaged in over the last decade [1]. In my last article, Measuring Maturity , I wrote about Data Maturity and how this relates to both Data Strategy and a Data Capability Review. I find Data Strategy creation a very rewarding process.





































Let's personalize your content