How a “PRACtical” Approach to Risk Management Will Aid COVID-19 Recovery Efforts
John Wheeler
SEPTEMBER 15, 2020
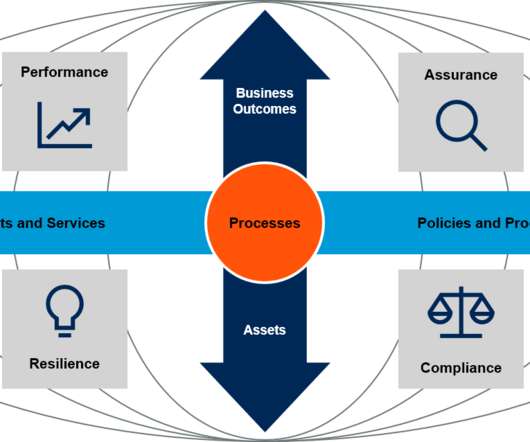
Those businesses that employ a “PRACtical” approach utilizing integrated risk management (IRM) will be in the best position to recover quicker and more successfully. A “PRACtical” Approach Provides a Balanced View of Risk. So, what is a “PRACtical” approach? IRM Technology Improves ERM.






















Let's personalize your content