Insights from Gartner’s 2023 Data Security Hype Cycle – Data Security Posture Management (DSPM) Highlights
Laminar Security
AUGUST 21, 2023
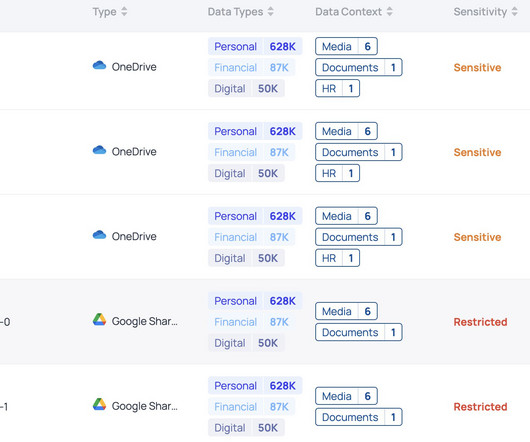
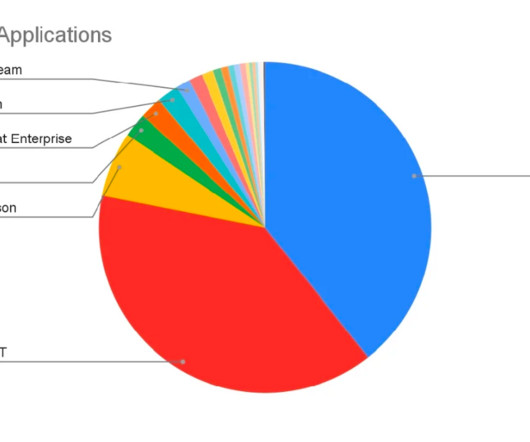
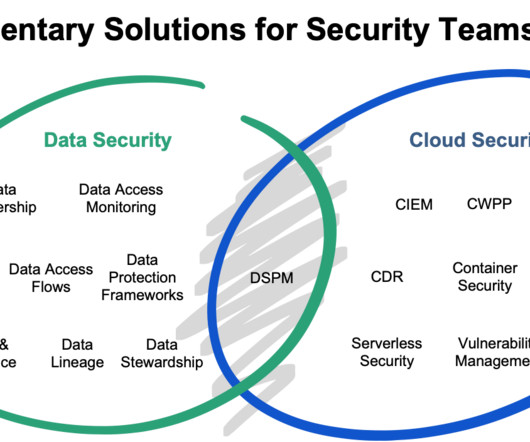
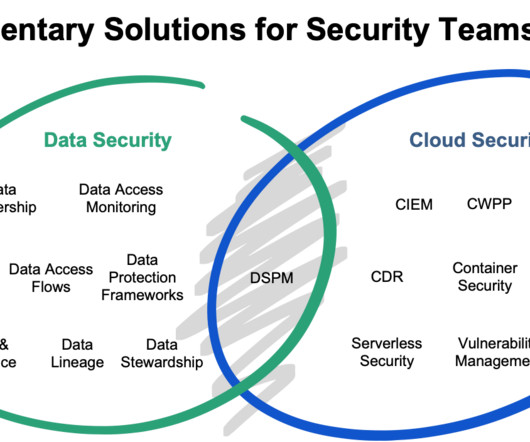
Introduction In the ever-evolving landscape of data security, staying ahead of emerging threats and challenges is critical for organizations. In this blog, we will delve into the key insights from the report and emphasize the significance of DSPM in shaping the data security industry.














































Let's personalize your content