Incorporating Data Analytics in Fast Food Legal Cases
Smart Data Collective
OCTOBER 8, 2023
Unraveling the intricacies of legal disputes in the fast food sector can be a formidable task. Harnessing the power of this technology can illuminate the path towards justice, bolstering the efforts of legal professionals. This article delves into the profound impact data analytics can have on fast food legal cases.



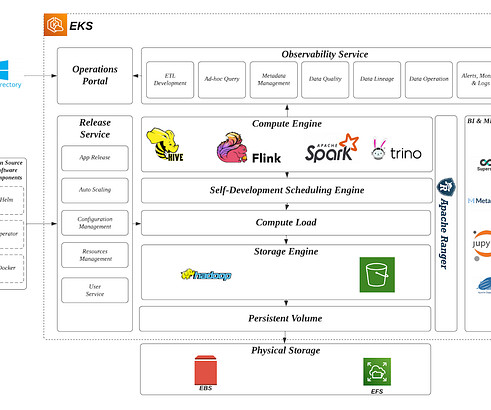





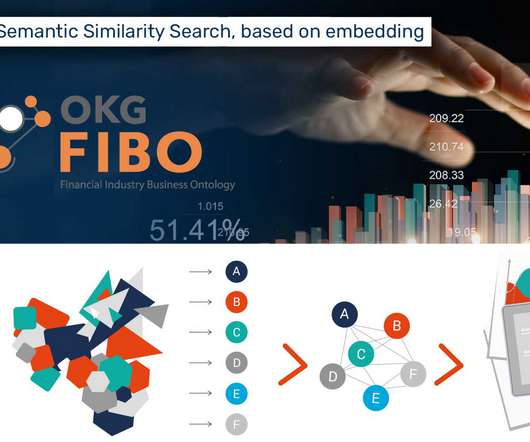





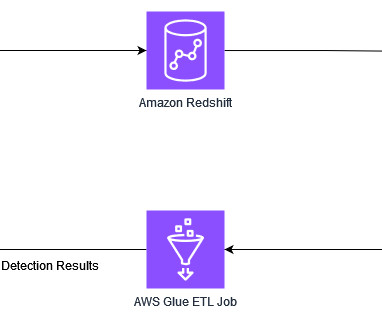





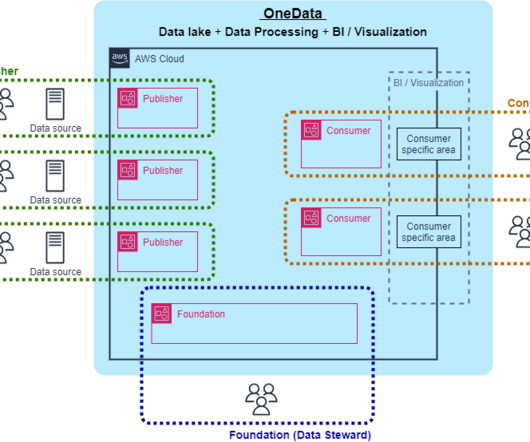












Let's personalize your content