Simplify IT operations with observability and AIOps
CIO Business Intelligence
MARCH 5, 2024
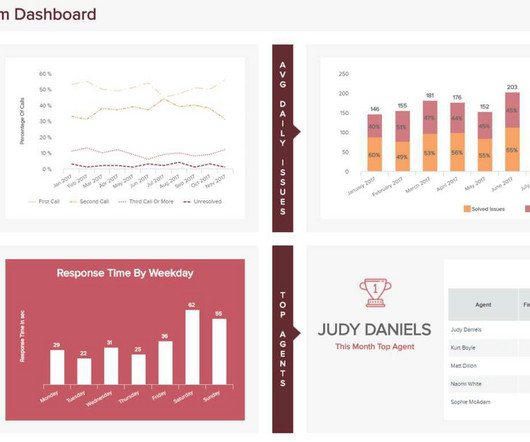
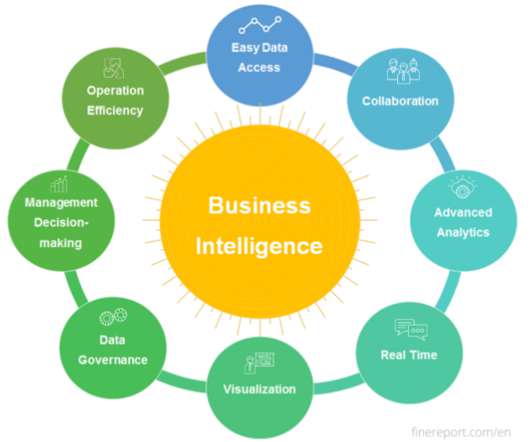
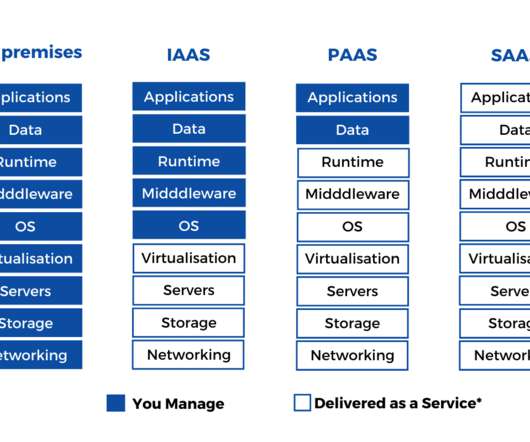
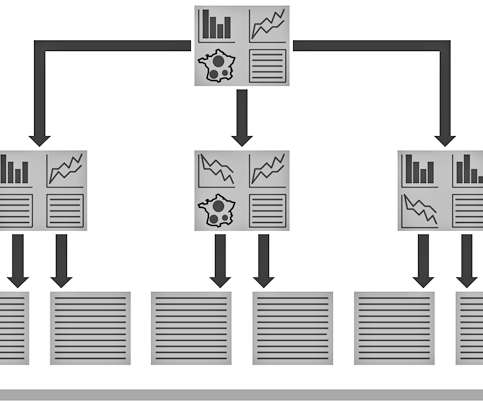
AIOps, combined with observability capabilities, helps unearth patterns in data to provide a holistic view of the entire environment. It also identifies issues before they become problems, and reduces the amount of noise generated by alerts, while automatically remediating low-level problems without requiring human intervention.










































Let's personalize your content