Google Account Security Breach: No Password Needed!
Analytics Vidhya
JANUARY 8, 2024
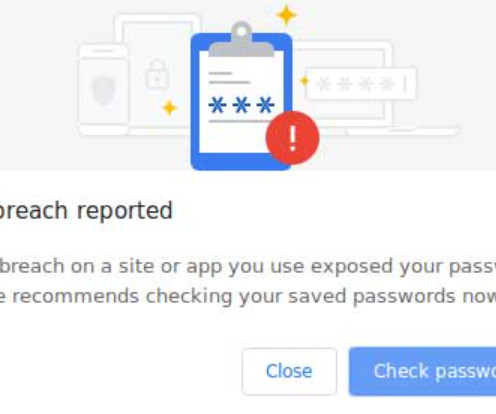
Google Account Security Breach!! Security researchers have unearthed a sophisticated hack that poses a grave threat to the security of Google accounts. This security breach, first revealed in October 2023, has prompted concerns about the vulnerability of […] The post Google Account Security Breach: No Password Needed!



















































Let's personalize your content