How to use data detection and response (DDR) to gain early warning into data leakage from insider threats
Laminar Security
DECEMBER 11, 2023
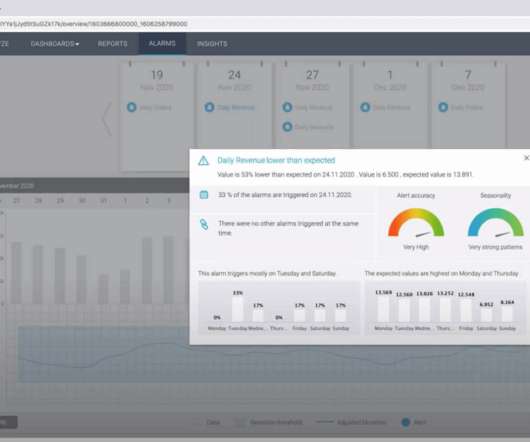
DDR is a data security solution that leverages artificial intelligence, machine learning, and behavioral analytics to monitor, detect, and respond to data activity across endpoints, networks, cloud, and applications. DDR covers all data sources, destinations, users, and behaviors. How does DDR work?












Let's personalize your content