7 Ways to End Dead Digital Weight on Your Website with Analytics
Smart Data Collective
JUNE 16, 2022
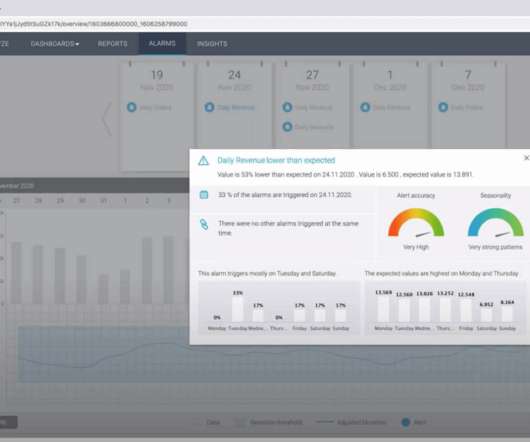
You can use sophisticated digital and behavior analytics technology. Analytics technology can measure the effectiveness of your website’s elements, reveal weak areas, and show you what needs improvement. Optimize your visual creatives. You will also want to use analytics technology to test different visual creatives.













Let's personalize your content