7 Ways to End Dead Digital Weight on Your Website with Analytics
Smart Data Collective
JUNE 16, 2022
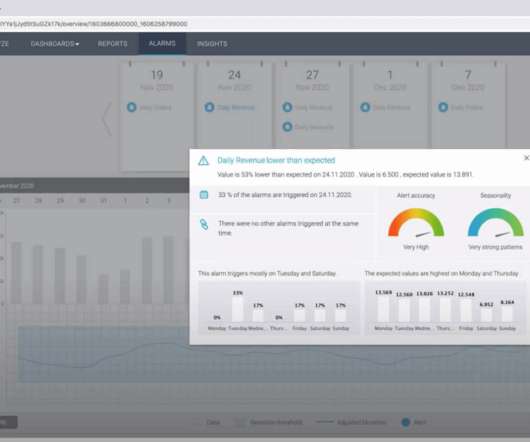
The first websites predated modern analytics technology. Google Analytics wasn’t launched until 2005. However, advances in analytics over the past decade have made it easier for companies to create quality websites. Keep reading to learn more about using analytics to optimize your website.













Let's personalize your content