Automating Model Risk Compliance: Model Validation
DataRobot Blog
MAY 26, 2022
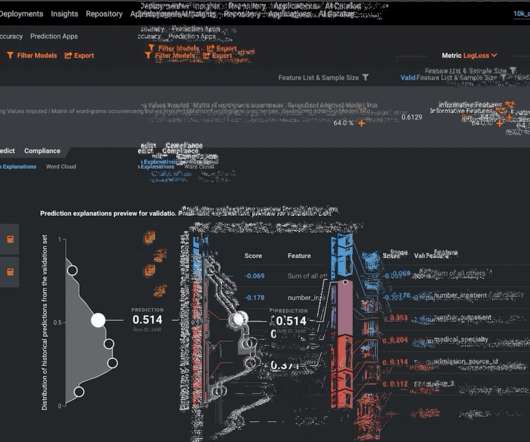
What are some steps that the modeler/validator must take to evaluate the model and ensure that it is a strong fit for its design objectives? Evaluating ML models for their conceptual soundness requires the validator to assess the quality of the model design and ensure it is fit for its business objective.
















Let's personalize your content