12 Cloud Computing Risks & Challenges Businesses Are Facing In These Days
datapine
MAY 31, 2022
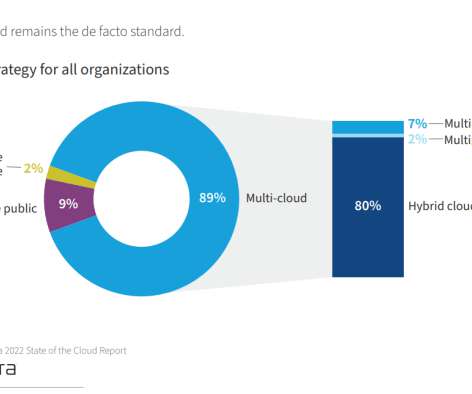
This increases the risks that can arise during the implementation or management process. The risks of cloud computing have become a reality for every organization, be it small or large. That’s why it is important to implement a secure BI cloud tool that can leverage proper security measures. Cost management and containment.















Let's personalize your content