Speed up queries with the cost-based optimizer in Amazon Athena
AWS Big Data
NOVEMBER 17, 2023
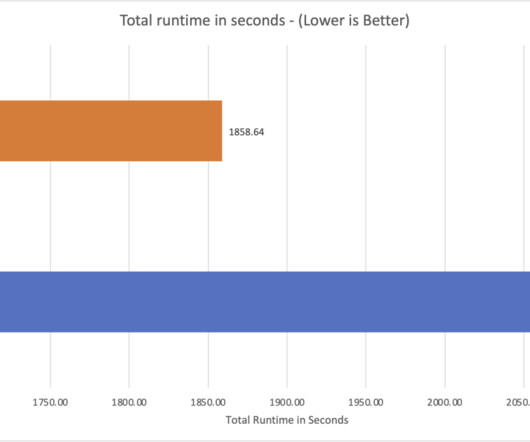
Doing it before risks unnecessary aggregation overhead because each value is likely unique anyway and that step will not result in an earlier reduction in the amount of data transferred between intermediate stages. Grouping after joining means a large number of records have to participate the join before being aggregated.



















Let's personalize your content