Email Marketers Use Data Analytics for Optimal Customer Segmentation
Smart Data Collective
OCTOBER 17, 2022
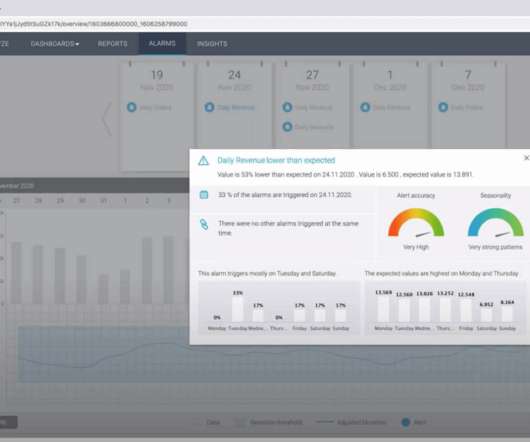
Using data analytics help your email marketing strategies succeed. Data Analytics’ Importance in Email Marketing. Like any other marketing strategy, you must measure email performance. Types of data analytics. There are four types of data analytics for various marketing reasons. Segmentation.















Let's personalize your content