Multicloud data lake analytics with Amazon Athena
AWS Big Data
MARCH 18, 2024
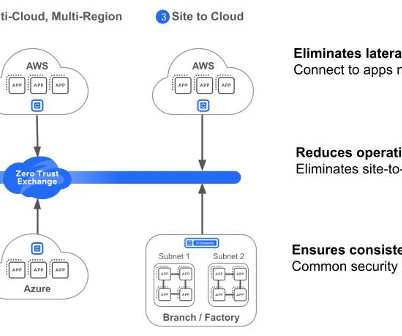
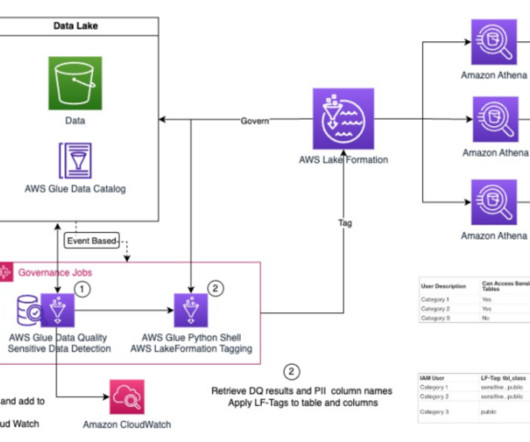
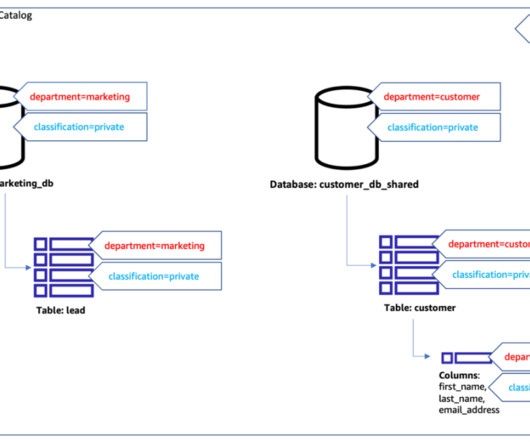
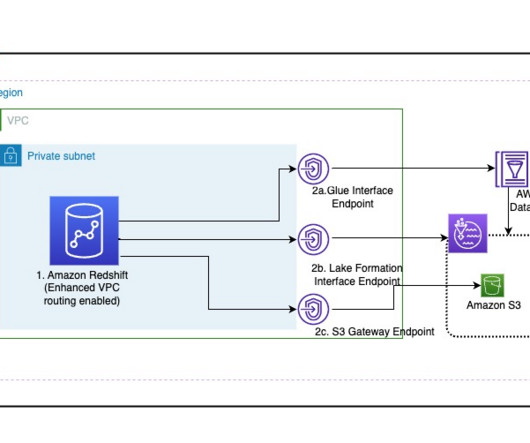
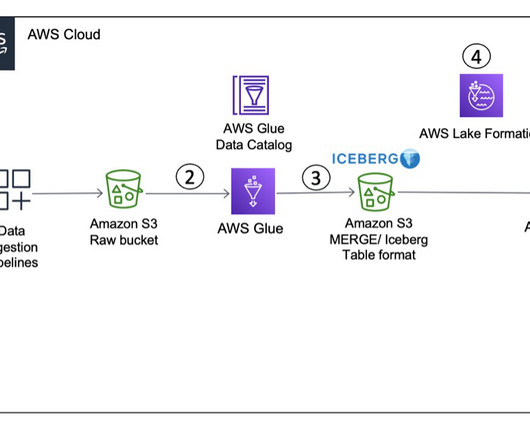
This could be for various reasons, such as business expansions, mergers, or specific cloud provider preferences for different business units. Additionally, we explore the use of Athena workgroups and cost allocation tags to effectively categorize and analyze the costs associated with running analytical queries.








































Let's personalize your content