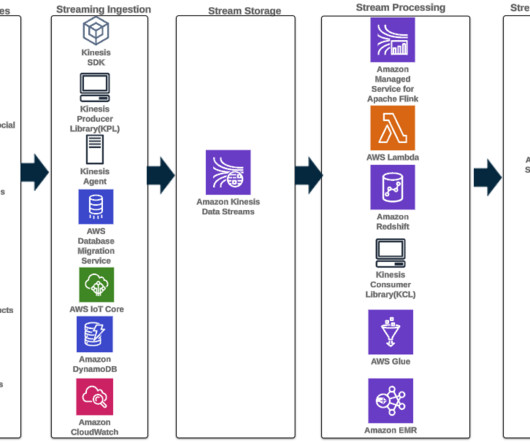
Modernize Your Data Architecture with Data Virtualization
Data Virtualization
DECEMBER 2, 2021
Practically overnight, organizations have been forced to adapt by modernizing their data architecture to support new types of analysis and new ways to connect to data. The post Modernize Your Data Architecture with Data Virtualization appeared first on Data Virtualization blog.


















































Let's personalize your content