Unleash the power of Snapshot Management to take automated snapshots using Amazon OpenSearch Service
AWS Big Data
OCTOBER 18, 2023
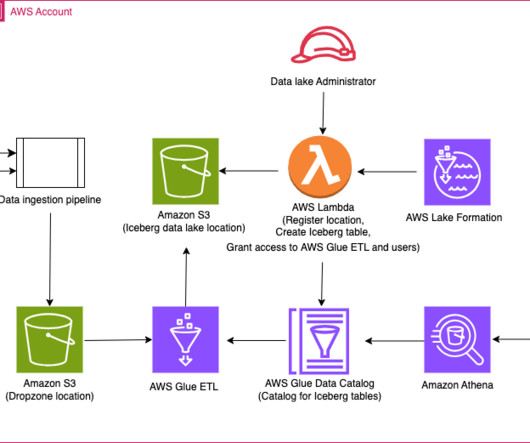
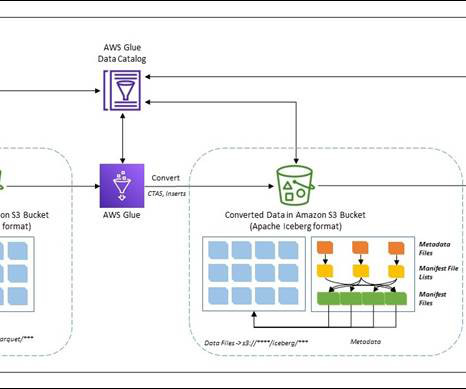
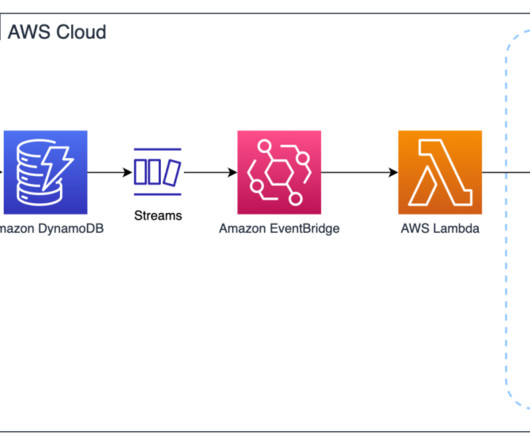
in Amazon OpenSearch Service , we introduced Snapshot Management , which automates the process of taking snapshots of your domain. Snapshot Management helps you create point-in-time backups of your domain using OpenSearch Dashboards, including both data and configuration settings (for visualizations and dashboards).












































Let's personalize your content