Empowering security excellence: The dynamic partnership between FreeDivision and IBM
IBM Big Data Hub
MAY 8, 2024
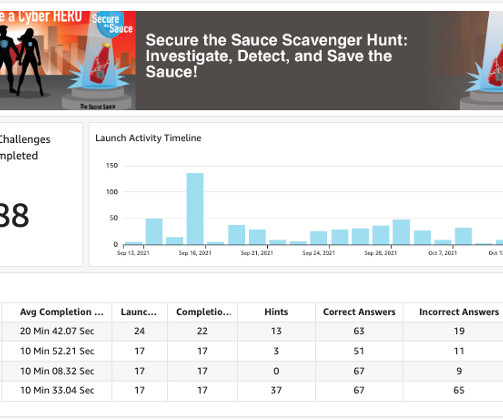
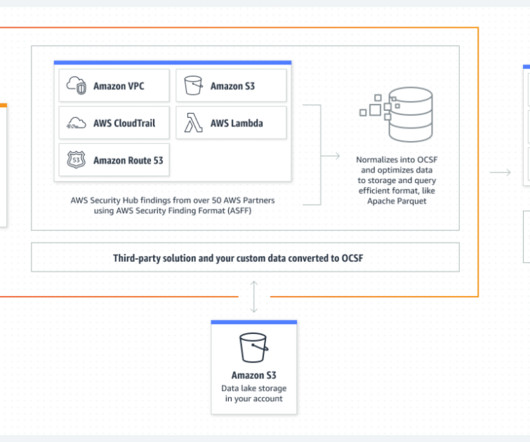
FreeDivision’s products and expertise distinctly stand out when conducting comprehensive security checks for clients. Its solution not only protects against threats, but also acts as a vigilant hunting tool. The response procedures use artificial intelligence to prevent human error and enable rapid response to threats.


































Let's personalize your content