Measuring Maturity
Peter James Thomas
MARCH 9, 2020
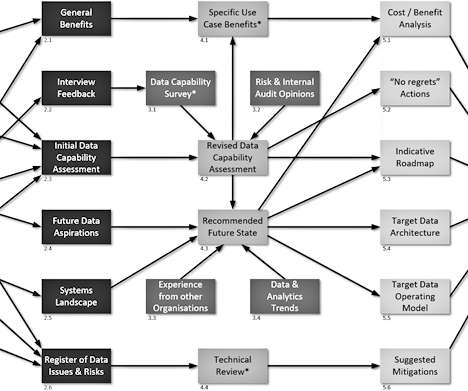
The author, engaged in measuring maturity – © Jennifer Thomas Photography – view full photo. In the thirteen years that have passed since the beginning of 2007, I have helped ten organisations to develop commercially-focused Data Strategies [1].
























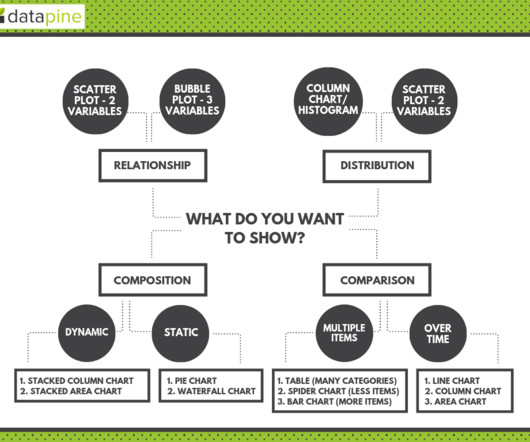

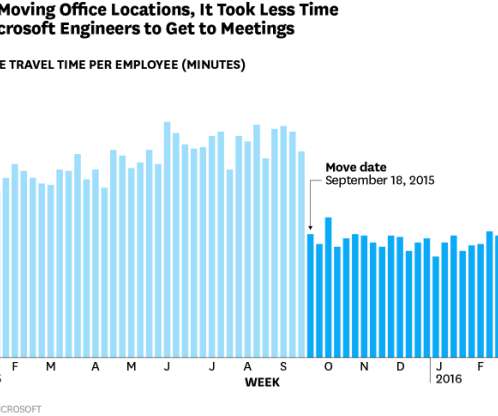











Let's personalize your content