How BMO improved data security with Amazon Redshift and AWS Lake Formation
AWS Big Data
MARCH 1, 2024
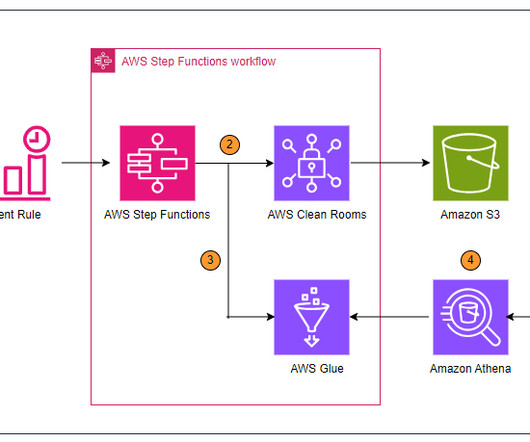
As they continue to implement their Digital First strategy for speed, scale and the elimination of complexity, they are always seeking ways to innovate, modernize and also streamline data access control in the Cloud. BMO has accumulated sensitive financial data and needed to build an analytic environment that was secure and performant.














































Let's personalize your content