A Data Prediction for 2025
DataKitchen
FEBRUARY 2, 2023
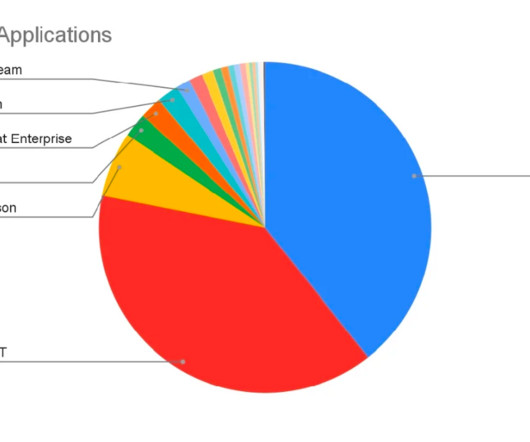
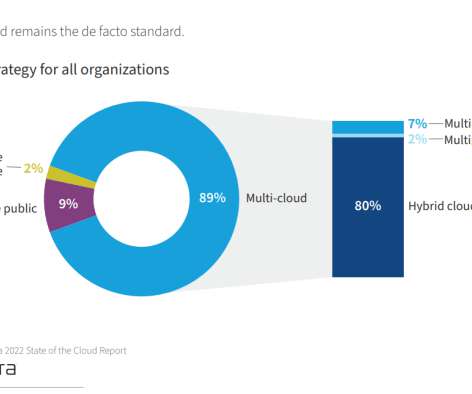
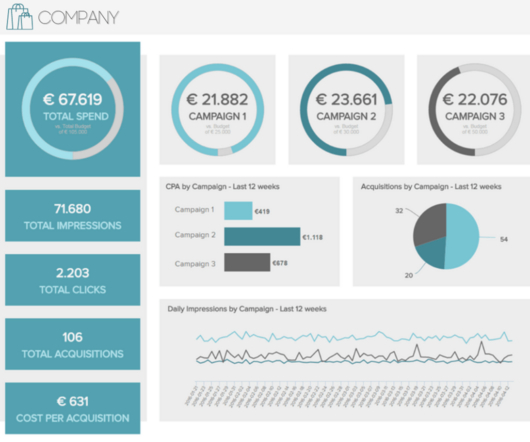
We’ve read many predictions for 2023 in the data field: they cover excellent topics like data mesh, observability, governance, lakehouses, LLMs, etc. What will the world of data tools be like at the end of 2025? Central IT Data Teams focus on standards, compliance, and cost reduction. Recession: the party is over.
















































Let's personalize your content