GDPR compliance checklist
IBM Big Data Hub
JANUARY 22, 2024
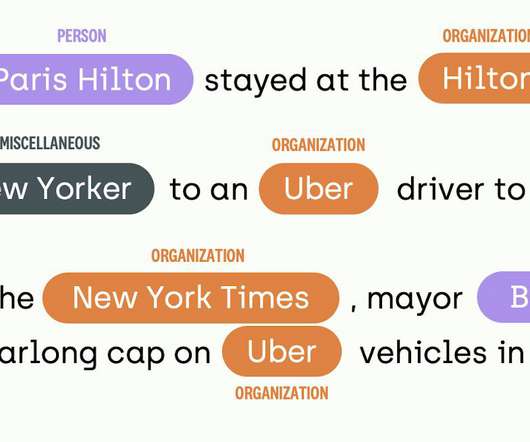
However, GDPR compliance is not necessarily a straightforward matter. The stakes are high, and the GDPR imposes significant penalties for non-compliance. To understand compliance requirements, organizations must understand what these terms mean in this context. The controller is ultimately responsible for ensuring compliance.


















































Let's personalize your content