Chart Snapshot: Radar Box Plots
The Data Visualisation Catalogue
MAY 2, 2024
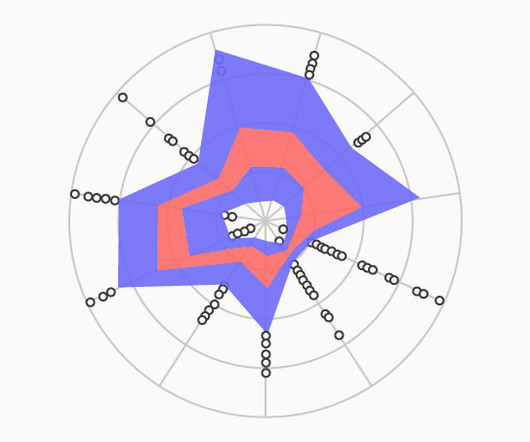
Analysing a Radar Box Plot can allow for predicting any classification confusion that may arise among classes and help in identifying strategies for improvement. This visualisation is most effective when dealing with tasks involving more than four relevant variables, as it can represent higher-dimensional data in a way that is still legible.









































Let's personalize your content