Why CISOs Need to Hire Data Security Experts & What to Look For
Laminar Security
NOVEMBER 1, 2023
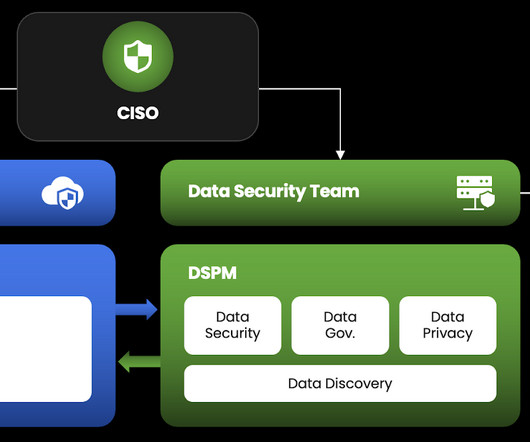
Because data is an invaluable resource for today’s businesses, CISOs need to consider data security a separate practice from their other security disciplines. It could be a center of excellence (COE) within a large enterprise, a smaller data security team at a medium-sized enterprise, or one dedicated professional for smaller organizations.















































Let's personalize your content