Top Solutions for Cybersecurity Regulatory Compliance
Smart Data Collective
OCTOBER 31, 2022
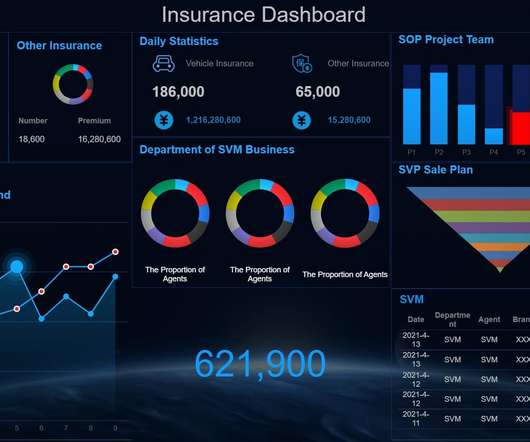
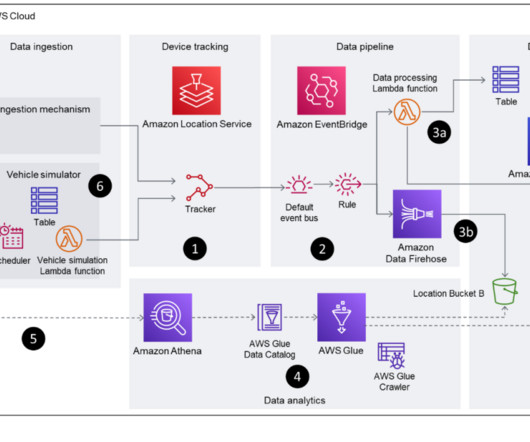
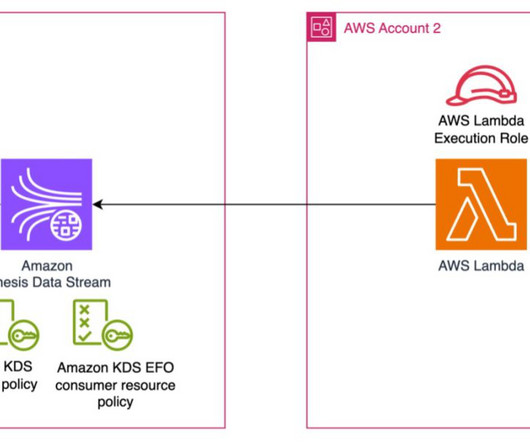
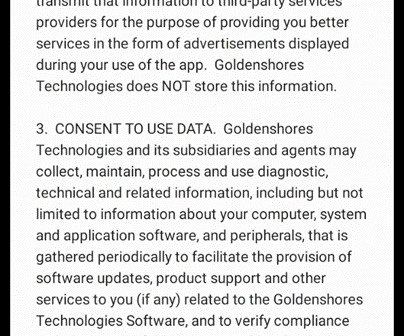
As the Internet of Things becomes increasingly instrumental in the workplace, company and consumer data risk grow. All it takes is for a team member to open a phishing email, download a malicious program, or conduct business on an unsecured device to cause an issue. Choose Hardware and Software Wisely.












































Let's personalize your content