Cloudera’s RHEL-volution: Powering the Cloud with Red Hat
Cloudera
MARCH 22, 2024
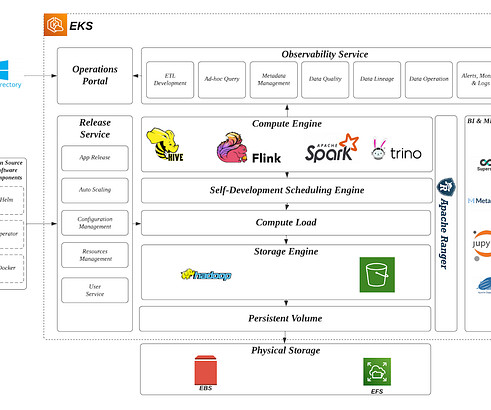
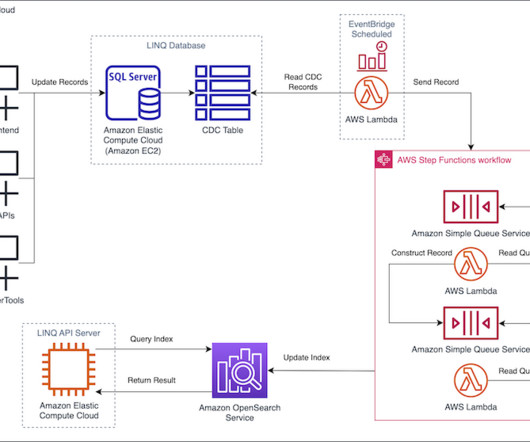
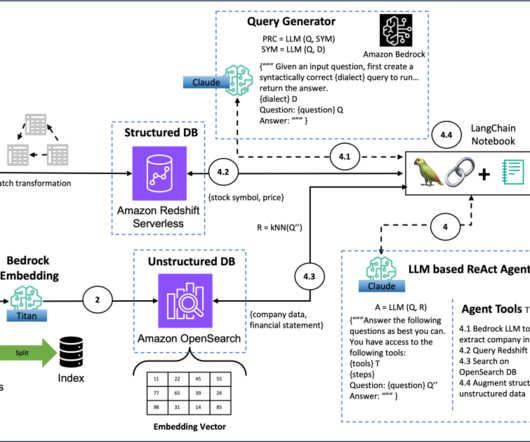
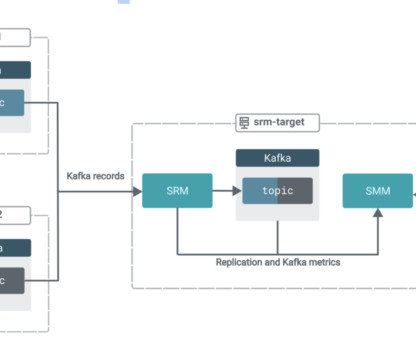
That’s why Cloudera and Red Hat , renowned for their open-source solutions, have teamed up to bring Red Hat Enterprise Linux ( RHEL ) to Cloudera on public cloud as the operating system for all of our public cloud platform images. Let’s dive into what this means and why it’s a game-changer for our customers.












































Let's personalize your content